Consumers want to enjoy the convenience of video anytime, anywhere, but such a wide range of video requirements has produced a large number of different streaming video compression standards to meet the requirements for different screen size resolutions and high bandwidth.
To provide video content support for so many different kinds of devices, many new sources of video streaming (and corresponding vendors) have been born outside traditional cable and satellite providers. Telephone lines, the Internet, and wireless communications, while supporting the development of streaming video, have also brought significant security issues to streaming video. In order to solve this problem, different streaming video sources have introduced and adopted more and more standard and proprietary encryption algorithms. However, the inconsistency of encryption schemes and implementation methods between different vendors leads to huge challenges in the design and support of video receiving devices.
FPGAs provide flexible solutions
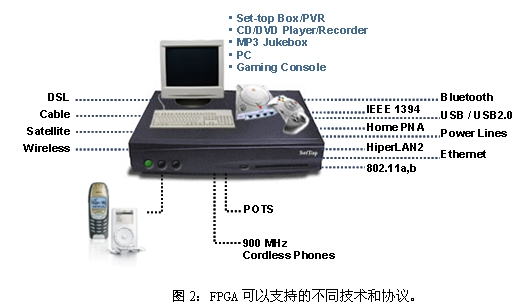
For many years, low-cost FPGA devices have become key components for set-top boxes and video gateways, providing video enhancement, missing pixel replacement, video conversion, product flexibility, and product differentiation. In addition, these devices also allow manufacturers to easily support different technologies and protocols, as shown in Figure 2.
The traditional flexibility of the FPGA platform and dedicated algorithmic functions are ideal solutions for solving a wide range of changing standards and proprietary encryption algorithms. Device reconfiguration capabilities can easily change the decryption algorithm as needed. With FPGA device reconfiguration, designs can use fewer logic gates and fewer devices to support more algorithms at a lower overall cost. The field upgradeability can quickly and easily cope with new algorithms and algorithm changes, thereby ensuring that the product is future-proofing and extending the life of existing products without the need for costly on-site replacement.
Hardware security issues
The concerns of video source providers have been confined not only to the security of the video stream itself but also to the security of the receiving hardware. Some video source providers are trying to define their licenses and video stream limits as systems that can provide secure video receivers. This requires many companies seeking to reduce the number of support and increase device-level security to further improve the overall design of the security level. The FPGA platform provided by the programmable logic device manufacturer Xilinx can solve this problem. The platform's DeviceDNA technology offers the ability to support multiple decryption algorithms and higher device-level security.
DeviceDNA allows device manufacturers to write a unique non-volatile factory serial number directly into the FPGA device. The ID of each device is different, so the design can be tied to a specific FPGA device. DeviceDNA can be used as the receiver's unique serial number, a unique license code, or in combination with a user-defined authentication algorithm written in the FPGA fabric to tightly bind a specific design to a specific FPGA device. If someone tries to clone or copy a certified design or write a bitstream to another FPGA device, the design will not be authenticated due to changes in the device's ID number. DeviceDNA is a 57-bit long serial number that can be read by the logic structure inside the device.
The close integration of DeviceDNA and user-defined authentication algorithms enables the required degree of security at a reasonable system cost. In the method of using the authentication algorithm, the key to security is the algorithm itself. In this method, certain parts of the security process must be kept confidential, in this case the user-defined algorithm itself. Since the algorithm is implemented in the PPGA logic structure, it becomes a few bits in the millions of configuration bits of the FPGA. Unless you know how these bits fit together or you know the algorithm itself, anyone who is trying to copy a design will look like just a bunch of numbers.
User-defined algorithms can be as simple or complex as the system requires—for example, simple hashing algorithms, or more sophisticated triple DES, AES64, 128, or 256-bit, or even fully-customized algorithms. At the same time, user-defined authentication algorithms can also be integrated into the receiver's authentication process. In this way, the receiving unit can be further bundled with the video stream system, the design, and the specific receiving unit, thereby further enhancing the security against cloning. In addition, the algorithm can be changed to support different video decryption protocol configurations, even using different algorithms between different models or different generations of products to further ensure security.
Increased safety impact on production
Hardware security issues also apply to production processes, especially board-level testing and verification. Therefore, the JTAG function is often removed in the design because the JTAG function makes the design lead to reverse engineering. Many companies use JTAG to shorten test time and increase system test coverage in the measurement and verification process. However, without JTAG, more tests are needed, especially system-level tests to ensure certain test coverage. Not using JTAG technology will increase production costs and ultimately affect the total system cost.
The problem with JTAG is the INTEST command, which checks the design's internal logic functions. When reverse engineering, this command can be used to determine the function of the design. Figure 3 shows a simple example where data is shifted into a register and the INTEST command is executed so that the data is clocked into the logic construct and into the next register and the result can be read. Since the overall design complexity can be reduced to smaller logic blocks, this command makes reverse engineering easier.

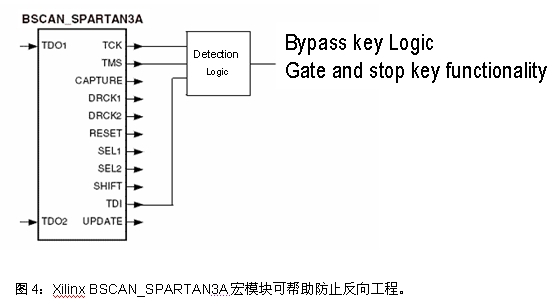
Some FPGA platforms help prevent this process from happening while still allowing the manufacturer to complete its pin-to-pin functionality. For example, in the Xilinx® Spartan®-3A platform, the BSCAN_SPARTAN3A macro block can be used in the design, and its detection logic can monitor the JTAG control signals in the FPGA fabric, as shown in Figure 4. If the activity of the JTAG control signal is detected, the user can immediately bypass the critical logic or turn off the key function in the design and no longer perform the correct function. In this way, reverse engineering personnel will read incorrect function modules and waste time and resources on solutions that cannot achieve the desired functions.
The DeviceDNA-enabled FPGA platform ensures the design security of the video receiver while also supporting the test and verification process, providing a cost-effective, high-quality security solution that supports a variety of different video streaming encryption protocols. For more information on DeviceDNA or JTAG, please refer to the Spartan-3 Series Configuration User Manual.
Economical Channel type fiberglass flexible Cable support tray Application
- Frp Cable Tray is Universally used in petroleum industry, chemical industry, electronic plant
- FRP Cable Tray is Suitable for some environment with high corrosion
- Modern factories and buildings with high floors
-
Any environment that need to be closed
Economical Channel type fiberglass flexible Cable support tray:
FRP cable tray is consists of a ventilated or solid bottom contained within longitudinal side members. Provides moderate ventilation with added cable support frequency and with the bottom configuration providing cable support every 4 inches. Available in metal and nonmetallic materials. Generally used with control and instrumentation cables in moderate heat generating applications with short to intermediate support spans of 5 feet to 12 feet. FRP cable tray bottom is available in flat sheet or corrugation that is 3 times stronger and 21 times stiffer than flat sheet bottoms. Corrugated seams between jointing sections eliminate need for bottom seam splices. Load Depths: 3" through 5-1/2" Materials available: Aluminum, hot-dipped galvanized Steel,Stainless Steel or figerglass.
Outdoor Cable Tray,C Channel Cable Tray,Aluminum Alloy C Channel Tray,Channel Type Cable Tray
Jiangsu Loncin Electric Equipment Co.,Ltd , https://www.loncincabletray.com