Introduction
Rowhammer has brought attention to the potential for hardware-based attacks that can cause significant damage. In a recent paper, Cai et al. proposed that similar vulnerabilities could exist in MLC NAND flash-based SSDs, potentially leading to serious consequences. In this article, we explore the requirements for a system-wide privilege escalation attack on SSDs and demonstrate file system-based methods to achieve such an attack. Specifically, we show how attackers can exploit interference between memory units to gain control, emphasizing the need for careful OS-level design.
Foreword
When developing software, hardware is typically abstracted away, and security features like resource isolation are taken for granted. Modern programming often requires little understanding of the underlying hardware complexity.
Rowhammer brings hardware's inner workings into focus. It exploits deeper flaws in memory management to breach sensitive areas. Recent studies have shown that such complex vulnerabilities can be exploited through JavaScript [8], enable privilege escalation on mobile devices [22], or even destroy co-hosted virtual machines.
However, DRAM isn't the only place where sensitive data resides. This data is crucial for implementing proper software security. File systems organize persistent storage, granting access based on disk-stored metadata. Flash memory has largely replaced traditional hard drives as the primary storage medium in modern computers.
Cai et al. recently suggested that a rowhammer-like attack could occur on solid-state drives, but no actual implementation was provided. We analyze the feasibility of such an attack from a system perspective. Specifically, we show that it is possible (though challenging) to use flash weaknesses to escalate local privileges under realistic assumptions about flash behavior and file system usage. Our demonstrated attack was not "system-wide" because it focused on the file system level and assumed damage to the underlying flash media. Nonetheless, we describe how this type of attack could extend to full system-level exploitation and plan to demonstrate this in future work.
More precisely, we use existing reliability mechanisms in SSDs (including ECC) to prove that attack primitives obtained from MLC NAND flash defects are coarse-grained. Unlike Rowhammer, which allows flipping a single bit, this attack enables the destruction of entire blocks. We then show that this weaker primitive provides sufficient control for an attacker to escalate privileges.
Model: We assume the target system runs a file system on an MLC NAND flash-based SSD and that the attacker has no privileged access, i.e., non-root user access. This allows the attacker to write to system memory through the file system. A typical scenario involves a non-privileged login shell. Physical access to the system is not considered.
Contribution: The main contributions of this article include:
(1) For the first time, we detail a complete, flash-based attack that elevates local privileges.
(2) We implement and demonstrate this attack at the file system level.
(3) We discuss the generalization and limitations of this attack.
Background introduction
2.1 Hardware-based Attacks
Table 1 categorizes hardware attacks. First, we distinguish between physical and non-physical attacks. Physical attacks require direct access to the system's hardware, such as detecting voltage levels or scraping silicon chips. Non-physical attacks exploit hardware without direct access, making them potentially more powerful. For example, timing bypass attacks can be executed remotely on cloud servers.
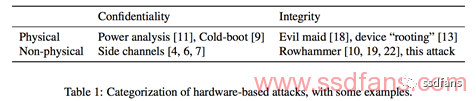
At an orthogonal level, attacks can compromise confidentiality or integrity. Confidentiality attacks involve reading primitives to expose sensitive information, while integrity attacks involve writing primitives to modify system behavior. Rowhammer is a notable example, using memory writes to escalate privileges on Android.
The attacks described in this article fall into the same category of non-physical hardware integrity attacks.
2.2 Flash Memory Defects
MLC NAND flash exhibits reliability issues due to media and device characteristics. Repeated program/erase cycles degrade reliability [23]. Inter-cell interference (CCI) occurs during page writes, affecting reliability. Due to capacitive coupling, programming voltages interfere with adjacent cells. Threshold voltage instability from frequent read operations increases bit errors [21]. Additionally, partially programmed blocks experience higher error rates before completion [14].
Attackers can exploit CCI to alter their own flash pages by programming adjacent pages with specific patterns. Due to CCI's nature, only certain state transitions are possible. Attackers can probabilistically modify adjacent victim pages with random changes.
2.3 Flash Reliability Mechanisms
Flash controllers use scrambling and error correction codes (ECC) to improve reliability. Data is encoded to reduce errors, and redundant bits are added for correction. Codeword lengths range from 512B to 2KB. Common codes include BCH and LDPC, though exact implementations vary by manufacturer.
System-wide Attack
A system-wide attack exploiting flash defects requires overcoming challenges across multiple layers of the storage hierarchy. From bottom to top:
(1) Flash chip: Inter-cell interference.
(2) Flash controller: Scrambler and ECC.
(3) SSD controller: Wear leveling and block placement.
(4) Operating system: File system caching and error detection.
(5) User: Privilege escalation.
Layer 1 forms the basis of the attack. As discussed in Section 2, previous research shows that bit flips can be induced in flash pages using inter-cell interference.
The flash community has long known about NAND errors, and manufacturers have designed controllers to reduce error probabilities. Layers 2 and 3 aim to provide a reliable abstraction to the OS, which may introduce vulnerabilities. Next, we explain what attackers might exploit from this abstraction.
The remaining challenges (Layers 4 and 5) focus on finding a file system-based attack vector that leverages this weak primitive, which is the main contribution of this article. The general idea is to corrupt the file system's data structures, create a new file system, and manipulate its structure to elevate permissions, such as creating a SUID root shell.
We explored various possibilities and introduced the most successful scenarios in Section 4.
3.1 Attack Primitives
The presence of ECC encoding/decoding determines the best outcome for an attacker: uncontrolled random modification of a flash page. To understand this, consider different decoding methods that inject raw bit errors into flash pages. Assume user data is protected by BCH encoding, which corrects t bit errors. When an error is introduced, three possible events may occur:
(1) Decoding succeeds if the number of errors is ≤ t.
(2) Decoding failure is detected if the number of errors > t and the binary vector is outside the decoding radius.
(3) No decoding failure is detected if the number of errors > t and the vector falls within the decoding radius of another codeword. In this case, corrupted data is returned as if the read was successful.
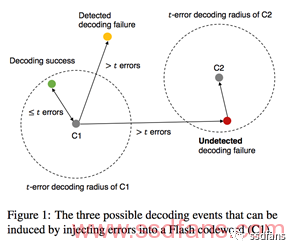
Figure 1 illustrates these decoding events. A successful attack must exploit undetected decoding failures. The attacker must inject enough errors to push the original readback mode into the decoding radius of an incorrect codeword. This leads to true data corruption, but the corrupted mode cannot be controlled at the bit level. The set of impairment modes depends on the number of error code words reachable via CCI. Possible attack primitives from strongest to weakest are:
(1) P1: Flip a single bit in a controllable position.
(2) P2: Uncontrollably flip a single bit within the block.
(3) P3: Uncontrolled random modification of the block (high bit flip, resulting in undetectable decoding failure).
(4) P4: A block is damaged (an error occurred while reading the block).
For DRAM rowhammer, P1 or P2 can be implemented, but since flash has strong ECC protection, P1 and P2 are unlikely here. P4 is extremely unlikely to be used for privilege escalation. We focus on P3, the only feasible attack.
FTL operations (such as wear leveling and garbage collection) and block placement algorithms must be considered when implementing an attack. Traditionally, FTL performs wear leveling to balance P/E cycles. An attacker can mitigate interference by repeating attacks. Garbage collection write operations may exceed user writes, so the attacker should wait for GC to complete before starting the attack. This is likely successful because SSDs prepare idle time for user writes.
To maximize parallelism, SSDs use dynamic block placement algorithms. These can block an attacker's attack if the attacked page is written immediately after the attacker's page. To alleviate this, the attacker should repeatedly write the attacker's page until it lands in the same flash block as the attacked page.
3.2 Test Platform
Our test platform includes a PCIe flash development board with FPGA and DRAM, a general-purpose CPU, and an MLC NAND flash chip. NAND flash programming, data scrambler, and ECC are fully implemented in the FPGA. The FTL runs on the FPGA and CPU. The board is connected to an x86-64 server running RHEL 6.7. We have full control over the hardware and software stacks, as well as Linux device drivers communicating with the device.

The reliability research of MLC NAND chips used in our test platform has been documented in previous work [14, 15, 16]. In the context of this work, the test platform was used to verify our understanding of MLC NAND flash behavior.
File System Layer Attack
We now describe the parts of the attack related to the file system (layers 4 through 5). Video demonstrating local privilege elevation: https://?v=Mnzp1p9Nvw0. Successful attacks require meeting the following constraints:
(1) R1: Data corruption of the target block should not (or with low probability) cause a fatal file system error, preventing the attack and requiring administrator intervention.
(2) R2: The target should be a block that is often written (to increase success chances). Ideally, the write should be triggered by the attacker. This allows timing of file system attacks from Layer 1 to Layer 3.
(3) R3: Data corruption of the target block should have sufficient possibilities to create available conditions.
(4) R4: The new cache should be refreshed to force the operating system to access corrupted data in the flash drive.
4.1 Environment Construction
We implemented an attack on Linux using the ext3 file system and installed it using default options. The file system does not need to be the root file system. We will discuss in Section 5 how these assumptions can be relaxed and promoted.
4.2 Attack
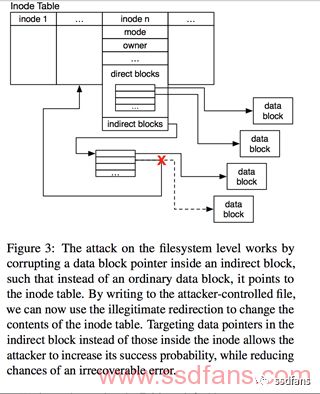
Considering the limitations of the attack, we chose the indirect block as the attacked block.
The indirect block of ext3 is a file system block size area containing data block pointers, each 4 bytes in size. In a 4K block size file system, the indirect block contains 1024 data block pointers. Once the file size exceeds 12 blocks, an indirect block is written (via the kernel file system driver): this makes it easy for the attacker to trigger.
If the lower layer of the attack (Layers 1 to 3) succeeds, the indirect block is destroyed. There are three possible outcomes for each of the 1024 data pointers in the indirect block.
(1) A 32-bit data pointer can point to an "interesting block" inside the file system (e.g., inode table, root ssh private key file, important binary used by root): this is the only available condition.
(2) A 32-bit data pointer can point to an "uninteresting block" within the file system, such as a data block in a file already owned by the attacker.
(3) The 32-bit data pointer can point to a block outside the file system (i.e., block number ≥ the number of blocks on the file system). In this case, the attack is not available. Fortunately, the file system kernel driver will return an error for the corresponding data access: subsequent accesses using the same indirect block will still succeed. If any of the 1024 corrupted blocks point to an interesting block, this behavior of the driver is effective for the attack, greatly increasing the probability of success.
Suppose the damaged pointer points to an inode table (available condition). An attacker can then create (or modify) an inode owned by a root user by simply writing the attack file (controlled by the attacker). Then, the attacker points the data block pointer of the inode to a shell data block and finally increases the permissions by executing the attack file (now a SUID-root shell, which requires the inod of the SUID-root shell to be flushed from the cache). As shown in Figure 3.
We have shown that R1 is compliant because randomly destroying the indirect block does not cause fatal errors. R2 is also compliant because the attacker triggers the writing of the indirect block pointer (by simply writing enough bytes to the file). We now show that the R3 constraint (the probability of creating a fully available condition) is also met.
The probability that a single data pointer points to the interested block is p1:

And the probability that any 1/4 block size attack pointer points to the interested block is p2:
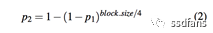
Assuming that only the inode table is "interesting" for the attacker and has a 100 GB file system with a 4 KB block size, the inode ratio for each inode (default is /etc/mke2fs.conf) 16384 bytes is:

Therefore, assuming that the attacker successfully crashes a block of data in the indirect inode, the privilege escalation attack will have a 9% probability of success. Therefore, we believe that R3 is more consistent.
Finally, we show that the cache can be refreshed by the attacker (R4). The attacker needs to flush the cache at two different times: to overwrite the contents of the inode table and execute the newly created SUID-root shell. In the first case, the cached data that should be culled from the cache is the indirect block, and in the second case, the inode. Attackers can naturally take two strategies: passive or active. Passively, an attacker can wait for the file system to be reinstalled (for example, on reboot), or concurrent activity on the system causes sufficient memory pressure to evict the indirect block and subsequent inodes from the cache. Proactive attackers trigger routes that create memory pressure: an attacker simply uses a program to allocate enough memory to encourage the operating system to evict file system metadata from the cache. This is the method we used in the demo. (The effectiveness of this method may vary depending on the VFS and page cache settings, but in our attack, the default setting for RHEL 6.7 is that the eviction is valid).
4.3 Exploring the Details
We now discuss some of the details that emerged in the actual process, but not the core of the attack.
First, as you can see from the above description, the attacker needs to know the data block number of a root shell. Although it can be found by reading from the inode table (by being attacked) and identifying the shell (e.g., by timestamp or file size), this is unlikely because the readable portion of the inode table is unlikely to contain the root shell. A simpler alternative is for the attacker to first create a shell copy in the target file, let the file system create and set the data block pointer, then set the SUID bit and make the file root by writing directly to the inode table.
Second, the attacker needs to be able to identify if the damage was successful, i.e., the indirect block pointer points somewhere in the inode table instead of somewhere else. In fact, this is easy to implement due to the structure of the inode table (for example, the markup of a regular file with default permissions is repeated every 256 bytes).
Third, an attacker can overwrite an existing inode or the inode of the file that will be created. If an attacker has no limit on the number of files they can create (which is usually the default for most Linux distributions), we can assume that we are always in the former situation. Then, the attacker keeps creating files until the file system runs out of inodes (all inode tables are full), then searches the file system (for example, using find) for a SUIDroot file and executes it: this is done in our demo attack. In the case where there is a limit on the number of files an attacker can create, although we have not tried it, the attack is still possible (by deleting the file, waiting for the inode to be reassigned to other users and creating a new file until the target inode is assigned to the attacker).
Finally, an attacker may not be able to access an existing inode through the file system (for example, it is in a subdirectory that the attacker cannot access). In practice, this simply means that the number of interesting blocks is lower than the number of blocks calculated in Equation 3.
4.4 Improved Attack Using Double Indirect Blocks
A very similar attack can be performed against the destruction of the double indirect block rather than the destruction of the indirect block. Although this attack is slightly more difficult to interpret, it is more likely to be successful and more flexible (full read and write capability for the entire file system: please note that this will still increase the permissions by creating a SUID-root file).
Each 4-byte pointer in the double indirect block points to an indirect block. Therefore, destroying the double indirect block may allow the attacker to completely control the contents of the indirect block. By selecting a pointer in the indirect block, an attacker can read and write anywhere in the file system.
The available condition here is that a pointer in the double indirect block points to the block owned by the attacker. For example, an attacker can create a very large file (across multiple blocks) on a file system to increase the likelihood that a damaged pointer will be attacked. In the event of a breach, an attacker can verify that they have an indirect block by populating large files with the address of the file system superblock (fixed block number and identifiable format). The attacker can then modify the contents of the large file by reading and writing the target file to access any block on the file system: by writing a large file to control the location of the write or read access (control the contents of the indirect block), by accessing the target file. Control access to content.
Suppose an attacker can create a 100 GB file in an ext3 file system with a block size of 4 KB (this is a reasonable assumption). This improvement gives the attack a success probability of 99.7% (obtained by using Equation 2). This is because the number of interesting blocks has increased greatly.
Discuss
5.1 Other File Systems
Although many of the attacks described in Section 4 can be adapted, they still rely on file systems that use indirect blocks, such as ext3, ext2, and some versions of the Unix file system (UFS1). The ext4 file system uses extensions (and NTFS) to essentially describe a data block as a tuple (starting file block, starting disk block, number of blocks). Although there may be an "extent block" in ext4 (more than 3 extents, ext4 starts storing extents in new blocks outside the inode, thus starting the tree structure), we believe that the probability of successful attack will be low because the extents are much larger (that is, the ext4 parser does not capture the possibility of random corruption): ext4 usually uses a 48-bit block number space instead of ext3's 32-bit). Therefore, it remains to be seen whether this attack will still work for other file systems.
5.2 Metadata Checksums
In addition, some file systems (such as ZFS and ext4, but not ext3) can choose to use metadata checksums. Obviously, file system metadata checksums, whether or not they use cryptographic hashes, can detect that file system metadata (for example, inodes or ranges) has been corrupted by the kernel file system driver to significantly reduce the probability of success.
Finally, we run e2fsck (a tool that checks (and corrects) ext3 file system metadata) after the indirect block is corrupted. As expected, e2fsck successfully detected that the file system metadata was corrupted, which would cause the administrator to detect the attack. Of course, e2fsck rarely runs. To stop an attack, it needs to run before the attacker gains root privileges and can correct file system metadata.
5.3 Other Attacks
Any program that accesses SSDs directly or indirectly (broadly speaking) can be the target of non-physical integrity attacks on SSDs. In this article, we consider the file system, but other attack vectors may also exist.
Unfortunately, due to the limitations of the P3 that the attacker received and the other limitations of the attack (R1 to R4), we were unable to find another real-world program that would most likely be used for privilege escalation. However, we cannot rule out the existence of this possibility and need further research in this regard.
Finally, as a job similar to Rowhammer and Gruss [8], it is worth considering whether the attack proposed in this article can also be used remotely through browsers and JavaScript. Since browsers do allow writing and reading of file systems (although indirectly) through local caching of web content, cookies, or using the HTML5 storage API, it may be feasible to extend the attack vectors described here to remote attacks.
5.4 Encryption and Integrity
The use of disk encryption (such as dm-crypt) should be able to fundamentally prevent the attacks presented here. More precisely, disk encryption does not prevent attacks from going through Layers 4 through 5 (because the attacker is overwriting metadata that will be transparently encrypted/decrypted by the operating system). However, this will make it impossible for an attacker to obtain P3 from defects in Layers 1 to 3. In fact, as described in Section 3, in order to bypass the ECC, the combination of the scrambler and the Flash page can only acquire P3 in a programming limit in one direction, and the attacker needs to control the data written to the disk. However, by using disk encryption, it is difficult for an attacker to do so without knowing the encryption key.
As mentioned earlier, metadata integrity prevents file system attacks that we provide. We note that in addition to ZFS, current file system encryption solutions typically do not achieve (encrypted) file content integrity due to performance considerations.
To Sum Up
In this article, we present and solve the issues that need to be addressed in order to take advantage of flash defects in real-world scenarios. Most importantly, we demonstrated the use of flash defect-based exploits to exploit file system metadata. Combining these two aspects forms a complete system attack method, and the theoretical success rate is reasonable enough in practice;
In future work, we plan to address the steps to overcome ECC to complete the implementation of our system-wide attack.
The JUK universal screw terminal block series has the typical features which are decisive for practical applications:
l The universal foot allows the terminal blocks to be easily snapped onto the NS35 or NS32 DIN Rail with G shape.
l Closed screw guide holes ensure screwdriver operation perfect.
l For terminal block with different wire cross-sectional areas, complete accessories are available, such as end plates, partition plates, etc.
l Potential distribution achieved by fixed bridges in the terminal center or insertion bridges in the clamping space.
l Same shape and pitch Grounding Terminal Blocks as the JUK universal series.
l Adopt ZB marker strip system,achieve unified identification.
Screw Din Rail Terminals,10 Sq Screw Electrical Terminal,Screw Din Terminal Block,Din Rail Sak Terminal Block
Wonke Electric CO.,Ltd. , https://www.wkdq-electric.com