In recent days, WannaCry ransomware has swept the world. At least 300,000 users have been recruited in more than 150 countries, causing losses of 8 billion U.S. dollars (about 55 billion U.S. dollars).
At present, a number of cyber security experts pointed out that the current state of the virus is only slightly alleviated due to a variety of reasons, but many Internet users, especially Chinese users, still face a risk threshold.
The well-known anti-virus software Kaspersky Lab in Russia also said that if the computer has been recruited, there is only one way - reinstall the system, but the encrypted file will be lost.
Faced with this sudden virus attack, what should we do as a universal Internet user to protect personal property? The NetEase Cloud Security (YiDong) Lab organized eight major issues in this regard, analyzed the worm's past and present, and proposed several effective countermeasures.
Question one: How has the infection been reduced?
If your computer is infected with a ransomware virus, or if your friends call for help, what can we do to minimize the impact?
First of all, this is a ransomware worm. The worm is characterized by automatic replication and dissemination through the Internet. Like in the movie "Busanhangxing", people who have been bitten by a zombie will become zombies to infect more. people.
So the first step is to disconnect the network and prevent your computer from infecting more computers.
Secondly, it is suggested that the users should format the hard disk to completely eliminate the worm virus on the hard disk, just like a complete cytotomy.
Then, reinstall the system and install the appropriate system patch.
Finally, you need to install antivirus software and update the antivirus software virus database to the latest version.
At present, the most common mistake that many people make is that they are lucky enough to continue to connect infected computers to the Internet and do all kinds of trial operations, or to think that paying ransoms can be decrypted. In fact, the ransomware worm encrypts RSA files on the computer. The characteristic of this encryption method is that as long as the encryption key is long enough, an ordinary computer needs hundreds of thousands of years to be able to crack it, which means that an individual is almost impossible to crack. Therefore, once the computer is poisoned, there is basically no room for recovery.

Question two: How do non-poisoned people rule out risk?
If you are lucky and have not been affected by this attack, then please do not do an ordinary melon crowd. As long as you are using the Windows system and have not updated the patch for a long time, there is still a great risk of poisoning. It is recommended that this risk be eliminated in advance through the "three-step method":
The first step: off the network. The ransomware worm needs to be spread through the network. Closing the network also cuts the virus's route of transmission. The most direct way for an ordinary desktop machine is to unplug the network cable. If you use a laptop at home, you can turn off your wireless network card. If you use a wireless router at home, you can also turn off the wireless router. Finally, you can also pass the wireless router. Switch off the network in a switched-on PC. Individuals can choose the corresponding method to perform network disconnection operation according to their own actual conditions.
The second step: close the port. The ransomware worm was attacked by scanning the Server Message Block/SMB on the computer, so closing the 445 port also closed the worm's attack gate. The action is divided into the following steps:
a. Open the Control Panel - System and Security - Windows Firewall, click on the left to start or shut down the Windows Firewall
b. Select Start Firewall and click OK
c. Click Advanced Settings
d. Click inbound rules and create a new rule. Take port 445 as an example.
e. Select Port, Next
f. Select a specific local port, enter 445, the next step
g. Select Block Connection, Next
h. Configuration file, select all, Next
i. Name, can be input arbitrarily
The third step: apply the patch. The first two steps belong to the paradigm, but they only temporarily prevent the ransom worm from attacking. If you want to cure the problem, you also need to promptly use the official system patch to plug the system loopholes. As early as March of this year, Microsoft provided a patch for this vulnerability. It is recommended that users turn on the system to automatically update and check for updates to install. If the automatic update fails, you can also manually download patches from Microsoft's official website for installation. Patch download address: https://technet.microsoft.com/zh-cn/library/security/ms17-010.aspx.
Question 3: Will cell phone poisoning?
To ensure that the computer is absolutely safe, will our more frequently used mobile phones be at risk?
The phone will not be affected by the ransomware worm. The ransomware worm uses Windows system vulnerabilities. The affected systems are Windows 2000 through Windows 10, and Windows Server 2000 through Windows Server 2016. The current mobile phone operating system is iOS, Android, Winphone, etc., does not belong to Windows, so it is not affected by the extortion worm.
Question 4: Why is the ransomware virus spread so quickly?
To understand this reason, we have to start with the principle of extorting a worm.
First, the vulnerabilities exploited by the WannaCry worm are very common. Most personal PCs still use Microsoft's Windows operating system. The Windows system opens the 445 port by default, and a large number of Windows users do not have the habit of regularly updating patches. This gives worms The spread provides a large number of hosts. Second, the traditional ransomware needs to rely on “cheat,†which means it is necessary to trick victims into clicking on an attachment, a web address, and so on. The worm can be self-propagating and self-replicating, which means it can actively detect and spread. This transformation from "passive" to "active" has caused a qualitative difference in the speed of transmission.
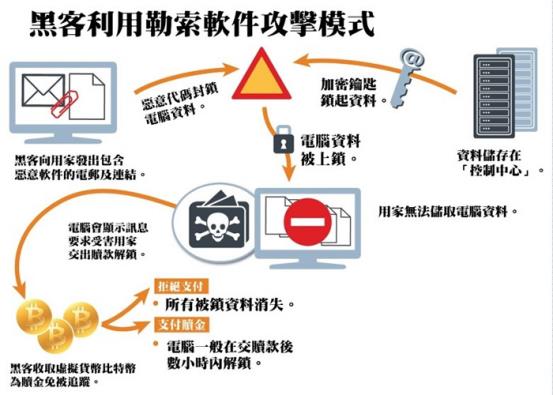
Second, WannaCry ransomware exploits a special vulnerability tool called "Eternal Blue" that sounds like the name of a precious diamond. The tool for this vulnerability comes from the NSA's cyber arsenal. On April 14 this year, a hacker group named "Shadow Middleman" once entered the US National Security Agency's network and exposed a number of archives of the Bureau. At the same time, it disclosed some of the cyber weapons used by the "formula hacking organization" under the Bureau. . According to reports, this network of weapons includes remotely exploiting about 70% of the world's Windows machine's exploit tools ("Eternal Blue"). After the emergency verification of these tools is true and effective. At that time, the incident caused a sensation in the security circle. Although Microsoft patched the vulnerabilities for a long time, it did not give alarm to enterprises and organizations, and a large number of enterprises and organizations did not install patches.
After the "Eternal Blue" tool was announced, it was immediately sought after because it can carry any virus to carry out automatic worm propagation. The most powerful one is the WannaCry virus.
Question 5: Why does WannaCry extortion work for Bitcoin?
In fact, the ransomware itself is not directly related to Bitcoin, and the reason why hackers demand Bitcoin for ransom payment is precisely the "globalization, decentralization, and anonymity of bitcoin in the payment transfer" advantages. ".
First of all, Bitcoin has a certain degree of anonymity, which makes it easy for hackers to hide their identities. Secondly, it is not restricted by geographical boundaries and can collect and transfer money globally. Once again, Bitcoin has the “decentralized†feature that allows hackers to automatically handle the process. Victims ransom.
As we all know, normal international remittances need to be reviewed by layers of foreign exchange control agencies. Transaction records will be recorded by many parties, including banks. Even if transactions exceed a certain amount, they must report to the relevant authorities to prevent irregularities such as money laundering. However, if you use Bitcoin to trade more easily, just enter the digital address, click a few mouse clicks, wait for the confirmation of the transaction, you can complete the transaction (at present, the country has suspended payment).
At the same time, Bitcoin currently holds the largest market share and has the best liquidity compared to other digital currencies. The recent sharp rise in bitcoin prices is also the reason why it is viewed by hackers.
Question 6: Why are public institutions such as schools, hospitals, and governments the hardest hit areas?
For this problem, perhaps the average user also has the intuitive feeling that the systems used in computer equipment in public institutions such as schools and hospitals are often the most backward, and even the speed is the slowest, coupled with the lack of professional and technical personnel, security Awareness is low. Computers of this type of organization cannot update patches in time and become the primary reason for being attacked.
Second, at present, most schools are basically a large intranet-internet LAN. Different services do not divide the security area. For example, student management systems, educational systems, etc. can all be accessed via any connected device. At the same time, IP addresses of laboratories, multi-media classrooms, and machines are mostly public network IPs. If schools do not have the relevant permission limits, all machines are directly exposed. The network that major universities and colleges usually access is the education and research network for education, scientific research, and international academic exchanges. For the academic purpose, most of the backbone networks do not take precautions against port 445. This has caused the university to become a hard-hit area. one of the reasons.
Question 7: Has the virus been contained? Will there be new variants?
From the current data analysis, the ransom worm has been contained, and the newly infected system is declining. At the same time, a foreign cyber security company has captured the 2.0 version of the virus, so it does not rule out the expansion of the new round of attacks. "Like earthquakes, there are often aftershocks. We need to be alert to various variants of the virus," but we only need to be prepared for defense and we need not worry about the latest system patches.
Question 8: What have we learned from this blackmail incident?
Weak security awareness is the most important reason for many people to recruit. After this incident, it is strongly recommended that online users should at least do the following four prevention tasks:
1. The important files must be backed up at any time, and can be backed up through the network disk, u disk and other media. If it is an enterprise, it can also set up a centralized file server for centralized management and backup of files.
2, the system must maintain the highest level of security, timely upgrade to the latest version, it is recommended to open the automatic update function. At the same time, the system needs to install anti-virus software to update the virus database.
3. Do not open strange files easily, especially files in strange emails and IM communication software.
4, install a genuine operating system, Office software, try not to use unexplained pirated software.
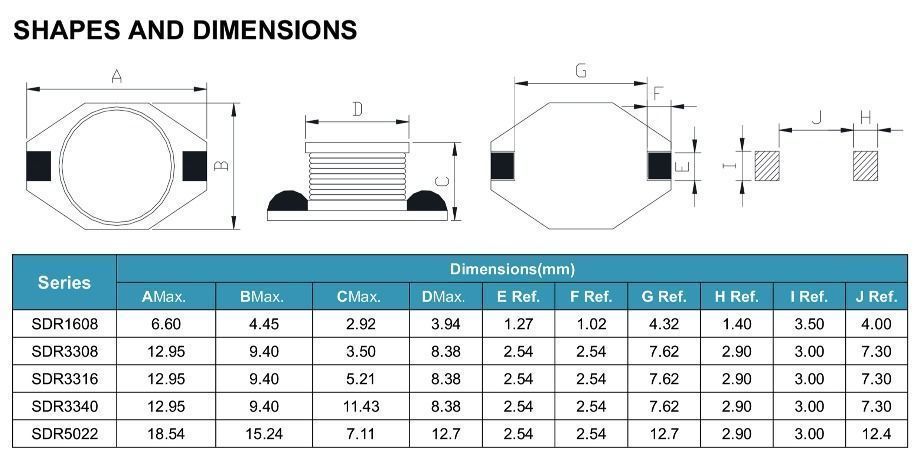
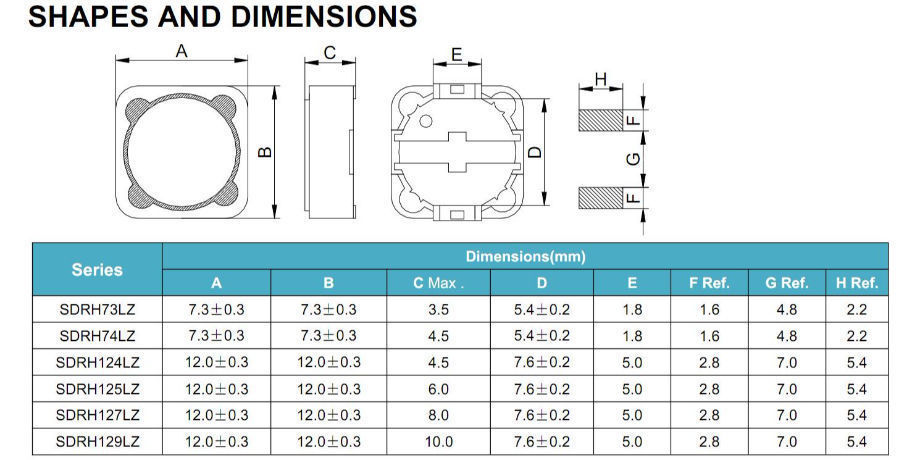
SMD/SMT Inductor(Coils)
An SMD inductor is a surface mount device inductor. It is a model of inductor that has no wire leads on its ends. This type of inductor is mounted directly to the surface of a circuit board via tining or soldering. They are positive reactance devices, available in many sizes and form factors optimized for particular applications. They are used in circuits that require filtering, power supplies, and many other functions. Inductance is associated with any PCB trace, via and ground plane and is usually considered a parasitic effect in all passive components and integrated circuits with wire bonds.ve components and integrated circuits with wire bonds.
Features:
â–ªIntegrally molded Power Inductor using a metallic magnetic material.Magnetic shield type and low noise
â–ªIt achieve large current,low Rdc,and compactness
â–ªGood performance in high-temperature environments with good DC superimposition characteristics
â–ªNo Halogen,RoHS compliant
Application:
Power supply around the PC,servers,communication devices,automotive electronics,compact power supply modules,others.






FAQ
1-MOQ?
We will work hard to fit your MOQ .Small purchase quantity is ok.
2-Payment term?
T/T, Western Union, Paypal, Credit Card
3-Delivery port?
Shenzhen, Guangzhou, Zhongshan, Hongkong.
4-Shipping date?
About 7 days when we check the payment.
5-Do you produce the core and bobbin by yourself .
Yes.we have 2 head company,1 subsidiary company.one is bobbin factory,one is core factory,last one is transformer factory.
6-Where is your factory?
In ShaanxI
Smd Inductor,Smd Power Inductor,Smt Power Inductor,Copper Wire Smd Inductor
Shaanxi Magason-tech Electronics Co.,Ltd , https://www.magason-tech.com